MAC addresses are one of those terms that few people know or they know it by another name. Some people mistakenly equate them to an Apple “Mac” computer or IP address. This unique bit of information defines devices connected to your network. And they can also add a layer of security.
What is a MAC Address?
As with many technical terms, MAC is an acronym. It stands for Media Access Control address. This is a 12-digit hexadecimal address that maps to a physical component. The hardware component could be a broadband router, wireless access card, network adapter, and so on. My smartwatch even has a MAC address.
The 12-digit number is unique but can have multiple names, including “networking hardware address” or “physical address”. And to confuse things more, Apple refers to them as a “Wi-Fi Address,” and my Android phone uses a “Phone Wi-Fi MAC address.
These numbers primarily work with network communications and help authenticate devices. For example, your Internet service provider may provide a router that associates that MAC address to your account. And, if you arbitrarily change the MAC address, you may lose Internet access. Typically, you would not change the address unless directed by some support rep.
The MAC Address Format
The number is assigned during the manufacturing process. The first half of the address represents the device manufacturer. It’s also called the Organizational Unique Identifier or OUI. So, for example, a MAC address starting with 00:16:CB is identified with Apple Inc. The second half is the serial number the manufacturer-assigned to the device.
The number usually shows as a series of hexadecimal digits like 00:16:CB:00:CD:E5 where each pair could be a letter or number. Sometimes the colons are omitted. And sometimes, you see hyphens. Regardless of the delimiter, the MAC address format differs from IP or IPv6 addresses.
How to Find a MAC Address
On a standalone network device such as a cable modem, there might be a sticker on the outside or stamped on someplace. However, on most Windows systems, you may find this information using the following steps:
- Press your Windows key + R
- In the Open: text box of the Run dialog, type cmd
- Click OK.
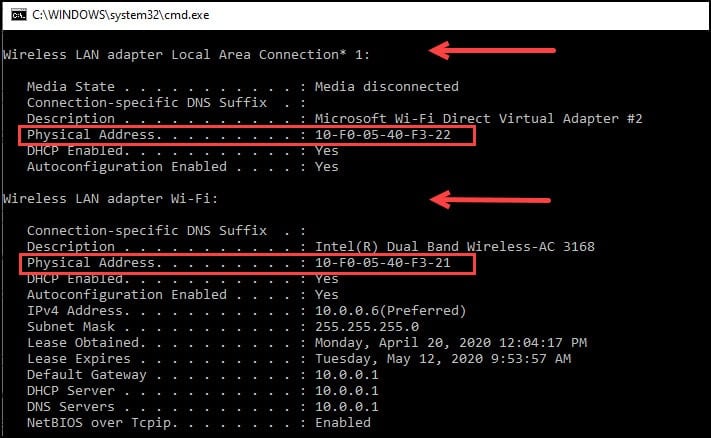
- At the command prompt, type ipconfig/all

- Press Enter.
Your computer should display a dialog similar to the one below. The line labeled “Physical Address” represents the MAC address. In some cases, you may see more than one MAC address. For example, you might see one for the built-in network card and another for a wireless one. However, you can only have one MAC address per device.
Another way to get MAC addresses is using the GETMAC / V command. This method is preferable if you need to grab the physical address and connection name on one line.

However, these commands show what is physically connected to my computer. It does not show me a wireless device that is connected to my network. For that, I need to use my router’s software.
MAC Address Lookup
Sometimes the descriptions you see for your devices don’t provide enough info. The last thing you want to do is to filter the wrong device from your network. Or, maybe you want to get more details. In these instances, it helps to query a MAC database. There are a number of them on the web, but I prefer the one by DNSChecker.org.
You type in the MAC address or the Organizational Unique Identifier in the textbox and press the Search button. The service can take MAC address examples using hyphens or colons.

The database won’t return what the device actually is, but it will give you the vendor name and address, which is a start.
MAC Address Filtering
Another layer of protection is MAC filtering. You may be familiar with blocking websites. However, MAC filtering is a way to allow certain devices to connect to your network. For example, your notebook, but not a guest’s.
In combination with your security settings, MAC filters can deter some hackers. You might think of this as adding a deadbolt to the latch bolt on your front door. People can still break down the door, but most won’t.
Since the MAC address is unique, it can be used as a filtering mechanism to keep devices on or off your wireless network. Most 802.11 wireless networks will allow or deny access to specific MAC addresses. In my case, I entered the MAC addresses for the devices that I would allow to connect to my network.
I enabled MAC filtering and entered the three MAC addresses to connect to my network on my router. Each of these MAC addresses belongs to a device that I use. If a device tries to connect with a MAC address that is not on that list, it will be blocked.
Using MAC filters in conjunction with other security settings on a wireless system is a stronger solution that will deter some from hopping onto your network. One disclaimer about MAC filtering is that it isn’t foolproof and shouldn’t be used as the only security measure. The reason is MAC addresses can be cloned. Sometimes people need to clone MAC addresses because of ISP configuration issues. The same mechanism that allows you to change a MAC address for your device also works for a hacker.
Another gotcha about these addresses is some operating systems allow you to randomize your MAC address. This is the case with some Android versions. As a result, you’ll have to continually update your allowlist for these phones or turn off the feature.
As with most security intrusions, the harder it is for someone to break in, the less apt they are to keep trying. Adding an extra security layer increases the time and equipment needed for a hacker to compromise your network. Hackers will likely start there since there are still many insecure wireless networks.
